LibTIFF could be made to crash or run programs as your login if it opened a specially crafted file.
An extremely convincing phishing attack that impersonates a multi-game skin trade bot appears to be using a fake Extended Validation TLS certificate to steal Steam accounts.

The phishing site displaying a fake Extended Validation certificate indicator.
The ongoing phishing attack impersonates TradeIt.gg, which facilitates the trading of skins, weapons and other in-game commodities within popular games like CS:GO, TF2 and DOTA.
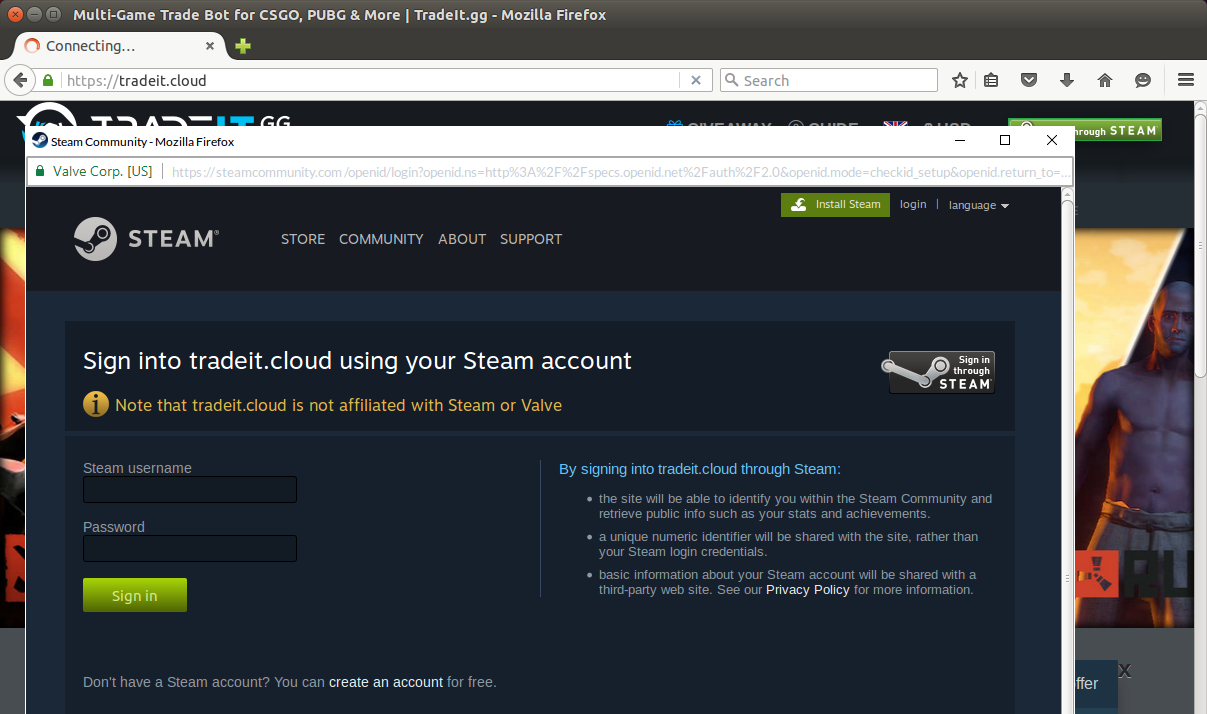
When a victim attempts to sign in through Steam to view their inventory on the spoof trading site, Steam’s OpenID login form opens in a new window, clearly displaying its use of an Extended Validation certificate issued to Valve Corp…
… or does it?
Extended Validation (EV) certificates offer the highest level of assurance that a website is being operated by a bona fide legal entity, which is why phishers like to make use of them whenever they can. EV certificates typically cost more than both domain and organisation validated certificates, as the issuance process involves a more stringent vetting process.
However, in this case, the fraudster has bypassed all of the expenses and vetting requirements by simply presenting a fake — yet very convincing — EV certificate indicator next to the address bar.
Closer inspection reveals that the Steam login page is also a spoof form, and it is not actually being displayed in a new browser window at all – it is being shown in an interactive, movable iframe that behaves like a window, allowing the fraudster to dress the “window” up however he likes. The tell-tale feature to look out for here is that the fake window cannot be maximized or moved beyond the boundaries of the spoof trading website.
Needless to say, when a victim submits their Steam credentials into this fake window, they will be stolen by a PHP script on the phishing site. The phisher can then monetize the compromised Steam account by selling it directly or by trading the victim’s valuable in-game commodities.
Fraudsters have a long history of exploiting user interface redressing vulnerabilities to make better phishing attacks. More than 14 years ago, Netcraft’s anti-phishing toolbar community discovered a particularly fiendish set of examples that exploited a vulnerability in Microsoft Internet Explorer, which allowed part of the webpage to be placed on top of the browser’s own address bar.

An extremely convincing PayPal phishing attack that took place back in 2005. A bug in IE made it possible for page elements to be placed outside of the browser’s viewport, allowing the attacker to place a fake paypal.com address on top of the browser’s real address bar, thus hiding the true location of the fraudulent website.
There are often resurgences in these types of attack, but the certificate and address spoofing techniques are usually forced to change as browser security improves and becomes more restrictive. No doubt there will be more attacks like these in the future, as phishing site developers continue to evolve new tricks.
Netcraft has been protecting consumers against phishing attacks for 15 years. You can enjoy the best protection against the latest attacks, including this Steam trading attack, by installing the desktop Netcraft Extension and Netcraft app for Android.
Kolab now integrates with Seafile, a cloud storage system. Find out what benefits this brings Plesk Premium Email customers.
The post New Kolab Releases (1): The Seafile Extension appeared first on Plesk.
WordPress 5.1.1 is now available! This security and maintenance release introduces 10 fixes and enhancements, including changes designed to help hosts prepare users for the minimum PHP version bump coming in 5.2.
This release also includes a pair of security fixes that handle how comments are filtered and then stored in the database. With a maliciously crafted comment, a WordPress post was vulnerable to cross-site scripting.
WordPress versions 5.1 and earlier are affected by these bugs, which are fixed in version 5.1.1. Updated versions of WordPress 5.0 and earlier are also available for any users who have not yet updated to 5.1.
Props to Simon Scannell of RIPS Technologies who discovered this flaw independent of some work that was being done by members of the core security team. Thank you to all of the reporters for privately disclosing the vulnerabilities, which gave us time to fix them before WordPress sites could be attacked.
Other highlights of this release include:
- Hosts can now offer a button for their users to update PHP.
- The recommended PHP version used by the “Update PHP” notice can now be filtered.
- Several minor bug fixes.
You can browse the full list of changes on Trac.
WordPress 5.1.1 was a short-cycle maintenance release. Version 5.1.2 is expected to follow a similar two week release cadence.
You can download WordPress 5.1.1 or visit Dashboard → Updates and click Update Now. Sites that support automatic background updates have already started to update automatically.
In addition to the security researcher mentioned above, thank you to everyone who contributed to WordPress 5.1.1:
Aaron Jorbin, Alex Concha, Andrea Fercia, Andy Fragen, Anton Vanyukov, Ben Bidner, bulletdigital, David Binovec, Dion Hulse, Felix Arntz, Garrett Hyder, Gary Pendergast, Ian Dunn, Jake Spurlock, Jb Audras, Jeremy Felt, Johan Falk, Jonathan Desrosiers, Luke Carbis, Mike Schroder, Milan Dinić, Mukesh Panchal, Paul Biron, Peter Wilson, Sergey Biryukov, and Weston Ruter.
poppler could be made to crash if it opened a specially craftedfile.