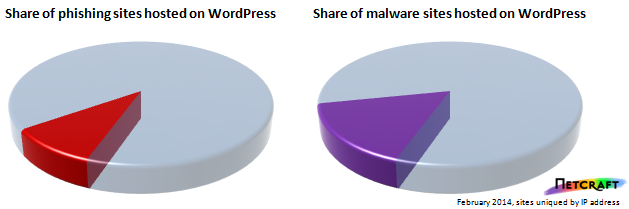
Compromised WordPress blogs were used to host nearly 12,000 phishing sites in February. This represents more than 7% of all phishing attacks blocked during that month, and 11% of the unique IP addresses that were involved in phishing.
WordPress blogs were also responsible for distributing a significant amount of web-hosted malware — more than 8% of the malware URLs blocked by Netcraft in February were on WordPress blogs, or 19% of all unique IP addresses hosting malware.
WordPress is the most common blogging platform and content management system in the world: Netcraft’s latest survey found nearly 27 million websites running WordPress, spread across 1.4 million different IP addresses and 12 million distinct domain names. Many of these blogs are vulnerable to brute-force password guessing attacks by virtue of the predictable location of the administrative interface and the still widespread use of the default “admin” username.
But remarkably, not a single phishing site was hosted on Automattic‘s own WordPress.com service in February. WordPress.com hosts millions of blogs powered by the open source WordPress software. Customers can purchase custom domain names to use for their blogs, or choose to register free blogs with hostnames like username.wordpress.com.
Automattic’s founder, Matt Mullenweg, was one of the original authors of WordPress when it was released in 2003. Automattic later handed the WordPress trademark to the WordPress Foundation in 2010, but still contributes to the development of WordPress. Such familiarity with the product likely explains why blogs hosted at Automattic are significantly more secure than average.
Bloggers can also go it alone — anybody can download the WordPress software from
wordpress.org and deploy it on their own website, and some hosting companies also offer “one-click” installations to simplify the process.
Bloggers who install WordPress on their own websites will often also be responsible for keeping the software secure and up-to-date. Unfortunately, in many cases, they do not.
Even well-known security experts can fall victim to security flaws in WordPress if it is not their core activity. For example, in 2007, the Computer Security Group at the University of Cambridge found their own Light Blue Touchpaper blog had been
compromised through several WordPress vulnerabilities.
Versions of WordPress after 3.7 are now able to automatically update themselves, provided the WordPress files are writable by the web server process. This has its own security trade-off, however, as an attacker exploiting a new and unreported vulnerability (a zero-day) that has the ability to write files will have free rein over the whole WordPress installation — an attacker could even modify the behaviour of WordPress itself to disable any future automatic security updates.
Insecure plugins
Over its lifetime, WordPress has been plagued by security issues both in its core code and in the numerous third-party plugins and themes that are available. One of the most widespread vulnerabilities this decade was discovered in the TimThumb plugin, which was bundled with many WordPress themes and consequently present on a large number of WordPress blogs. A subtle
validation flaw made it possible for remote attackers to make the plugin download remote files and store them on the website. This allowed attackers to install PHP scripts on vulnerable blogs, ultimately facilitating the installation of malware and phishing kits.
Similar vulnerabilities are still being exploited today.
Many of the phishing sites blocked in February were still operational this month, including this Apple iTunes phishing site hosted on a marketing company’s website.

Dropzones for WordPress phishing content
Note that the above phishing content is stored in the blog’s wp-includes
directory, which is where the bulk of the WordPress application logic resides. More than a fifth of all phishing content hosted on WordPress blogs can be found within this directory, while another fifth resides in the wp-admin directory. However, the most common location is the wp-content directory, which is used by just over half of the phishing sites.
The wp-content directory is where WordPress stores user-supplied content, so it is almost always writable by the web server process. This makes it an obvious dropzone for malware and phishing content if a hacker is able to find and exploit a suitable vulnerability in WordPress, or indeed in any other web application running on the server. Shared hosting environments are particularly vulnerable if the file system permissions allow malicious users to write files to another user’s wp-content directory. Some examples of directory structures used by phishing sites hosted in this directory on WordPress blogs include:
/wp-content/securelogin/webapps/paypal/
/wp-content/plugins/wordpress-importer/languages/image/Google/Google/
/wp-content/uploads/.1/Paypal/us/webscr.htm
The wp-includes and wp-admin directories can also be written to by other users or processes if the WordPress installation has not been suitably hardened. Failing to harden a WordPress installation and keep all of its plugins up to date could result in a site being compromised and used to carry out phishing attacks. Enabling automatic background updates is an easy way to ensure that a WordPress blog is kept up-to-date, but a significant trade off is that every WordPress file must be writable by the web server user.
Some other examples of directory structures seen in phishing sites hosted on WordPress blogs include:
/wp-includes/alibaba_online/
/wp-includes/www.paypal.com.fr.cgi.bin.webscr.cmd.login.submit.login/
/wp-includes/js/online.lloydsbank.co.uk/ /wp-admin/js/www.credit-mutuel.fr/
/wp-admin/maint/RBS-Card/index.html
/wp-admin/Googledoc/
Interestingly, the wp-admin directory appears to be the favourite location for Apple phishing sites – these make up more than 60% of all phishing sites found in this directory.
Vulnerable WordPress blogs can also be used for other nefarious purposes. A botnet of more than 162,000 WordPress blogs (less than 1% of all WordPress blogs) was recently involved in a distributed denial of service (DDoS) attack against a single website. Attackers exploited the Pingback feature in these WordPress blogs (which is enabled by default) to flood the target site with junk HTTP requests, causing it to be shut down by its hosting company.
A quarter of the phishing sites hosted on WordPress blogs in February targeted
PayPal users, followed by 17% which targeted Apple customers.
Please contact us ([email protected]) for pricing or further details about any of our anti-phishing and web application security testing services.

