(Jul 2) Several security issues were fixed in the Linux kernel.
(Jul 2) Several security issues were fixed in the Linux kernel.
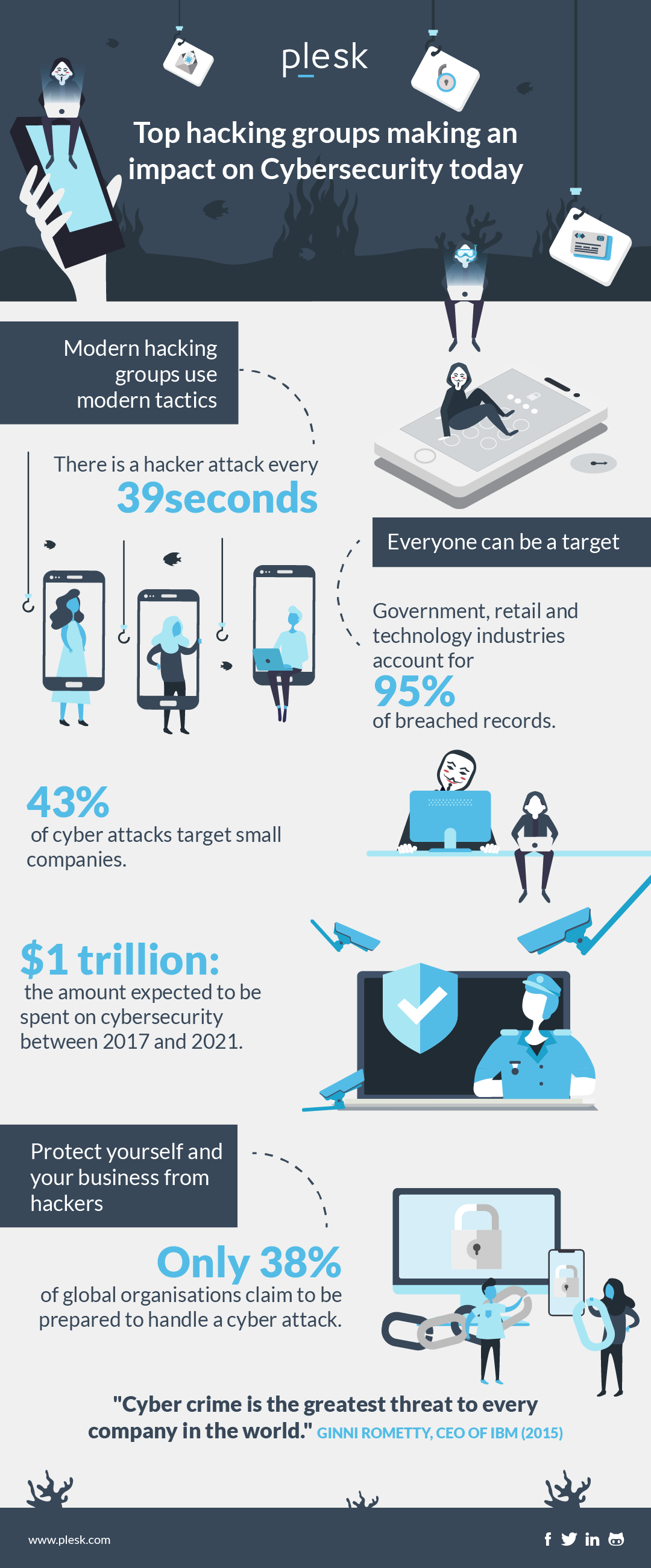
Top Hacking Groups impacting Cybersecurity today
Who are the top hacking groups threatening cybersecurity right now? Hacking methods are constantly evolving and becoming alarmingly advanced. They’re successfully targeting even the toughest cybersecurity systems.
Top hacking groups constantly update their strategies, target different organizations and change tactics to gain unauthorized access to sensitive info. So it’s no surprise that many organizations think keeping track of which groups they need to defend themselves against seems like an impossible task.
Modern top hacking groups use modern hacking tactics
Modern hacking groups are super difficult to hunt down, and modern technology is to blame. Different hacking groups target organizations, ranging from giants like Facebook and Twitter, to hacktivists with political ends that follow their own moral code.
There are some common techniques that modern hacking groups or hacktivists use. Including installing software like Keylogger to record the target’s key sequence. And keyboard strokes that capture every piece of sensitive info you type.
DoS or DDos (denial of service or distributed denial of service) is also popular. Hackers use it to take down a site or server by creating too much traffic on it. So it crashes down because of the overload.
Another one’s Phishing. Where a hacker replicates a popular site and lures users through spoofed links. When the target enters data or tries to log in, the hacker gets access to that sensitive info.
Everyone can be a target
Today’s most prolific and dangerous hackers are backed up by nation-states. So even organizations with the highest cybersecurity systems aren’t safe from these notorious groups. Groups like Comment Crew, Lazarus, and Fancy Bear are famous for historic hacks on the largest organizations and companies. Ones where even employees were victims. Read on to find out what you can do to protect yourself against hacking groups.
Comment Crew
Comment Crew is a Chinese hacking group, also known as the Shanghai Group. Many believe they’re responsible for a number of China’s alleged cyber attacks since 2006. One of their biggest, although not so well-known, successful hacking attempt was on the company Coca-Cola.
They sent a malicious email from, what looked like, Coca-Cola’s CEO to the company’s deputy president. Once opened, malware smoothly downloaded onto his computer. Thus giving the hackers full access to everything he typed, through the installation of a keystroke logger. The hackers had access to sensitive files for a whole month before the FBI informed Coca-Cola of the breach.
Fancy Bear
Fancy Bear, also known as Sofacy, Pawn Storm or APT28, act out of Russia and Eastern Europe. Many suspect they’re backed by the GRU, Russia’s military intelligence agency. And they’re famous for interfering with European election results again and again. Like the 2017 breaches in the Democratic National Committee’s system during the presidential elections, for example.
Their rivals, Cozy Bear, also known as CozyDuke or Office Monkeys, has also infiltrated US think tanks. And they represent the Russian Federal Security Service (FSB), replacing the former KGB. Fancy Bear uses spear phishing and zero-day vulnerabilities, and they mostly target web-based email services.
Anonymous
Anonymous originated discreetly on the message boards of 4chan in 2003. They’ve grown massively and are one of the most powerful hacktivists, with the stated aim of protecting the freedom of the internet. Their location is completely unknown and this is where they draw power from. Because they’re completely decentralized, they can operate uninterrupted, even if one of their members gets arrested.
One of their most famous hacks was their anti-child pornography movement, and some of their campaigns involved their physical presence too. They’re usually immediately recognizable by their famous Guy Fawkes masks. There are over 100 hacking attempts attributed to Anonymous. But one of their most famous ones is their attack of the Islamic State’s social media accounts and online recruitment systems. They managed to destroy months of recruitment work.
Needless to say, they’re one of the powerful hacking groups who target equally powerful organizations. And they have very clear political and social aims motivating their hacks.
Lazarus
This hacking group is also associated with North Korea. They started hacking corporations in 2009, using DOS attacks on websites. We don’t know much about the group. But they associated themselves with many significant attacks on large corporations, where they used advanced hacking techniques.
In 2014, they successfully hacked Sony Pictures, causing their site to crash for several days. They accessed unreleased films and even the personal info of around 4,000 Sony employees. This was one of biggest corporate breaches at that time. But the group identified themselves as the ‘Guardians of Peace’, revealing some fishy practices at Sony.
This year, Lazarus attacked cryptocurrency users in South Korea using spear phishing. And they exploited vulnerabilities in a South Korean word processing software. Users fell victims to malware traps which stole their email addresses and passwords once the malware was opened.
Protect your business and self from hacks like the top hacking groups’
Cyber attacks are unfortunately a scary and undeniable reality today. While these hackers are stealthy, intelligent, and too often successful, there are ways to protect your company or business against hackers.
Security needs to be an integral part of your company. And that’s why it pays to teach employees cyber attack risks and how they might unknowingly jeopardize the company. Train employees to know what email and what attachments they should and shouldn’t download. And what internet practices are best. You should also protect all sensitive information with heavy encryption.
Finally, become aware of any potential risks to your cybersecurity. You can protect yourself against hackers the most when you learn the most common hacking techniques cyber criminals, and even top hacking groups, use.
The post Top Hacking Groups impacting Cybersecurity today appeared first on Plesk.
(Jul 1) Update for security fixes
(Jul 1) Upstream announcement: The phpMyAdmin team is pleased to announce the release of **phpMyAdmin version 4.8.2**. Among other bug fixes, this contains an important security update and it is highly recommended that all users upgrade immediately. The urgent vulnerability allows an authenticated attacker to exploit a phpMyAdmin feature to show and potentially execute files on the