(May 31) Update to 66.0.3359.181. Security fix for CVE-2018-6085 CVE-2018-6086 CVE-2018-6087 CVE-2018-6088 CVE-2018-6089 CVE-2018-6090 CVE-2018-6091 CVE-2018-6092 CVE-2018-6093 CVE-2018-6094 CVE-2018-6095 CVE-2018-6096 CVE-2018-6097 CVE-2018-6098 CVE-2018-6099 CVE-2018-6100 CVE-2018-6101 CVE-2018-6102 CVE-2018-6103 CVE-2018-6104 CVE-2018-6105 CVE-2018-6106
(May 31) An update for xmlrpc3 is now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability
(May 31) An update for xmlrpc is now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability
Every project, program and offering that Plesk provides is only as good as individuals behind the scenes. All of them are deserving. But today we want to pay homage to the ones racing against the clock to support all our partners worldwide. You guessed it – the Plesk Partner Success Team.
These heroes also manage our Plesk Partner Program which gives our partners more bang for their buck. I mean, there are exclusive discounts, global exposure, premium support, Licence API, and marketing resources, to name a few. You can resell Plesk, use Plesk or develop for Plesk – and still join our network of over 2,600 Plesk Partners. And moreover, the Plesk Partner Success Team will be there every step of the way.
Here’s the Plesk Partner Success Team
Discover who they are, and what makes them the most qualified for you and your goals. But most importantly, find out what makes our Pleskians in the Partner sphere different.
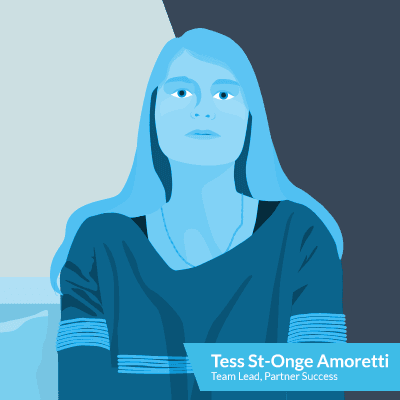
Partner Languages: Spanish, French, Italian, English, and more.
Fun fact about Tess: She runs on craft beer.
Tess
Say hey to Tess, our French-Canadian. As the Plesk Partner Success Team Lead, she’s always here and ready if any escalation is necessary. Tess directly manages the larger Partner accounts in Europe. But this is just a handful of what she does. She mainly works with the partner team, day in day out, to assist everybody with their own partners. Even during calls. She even helps investigate how we can help our partners grow and approach new prospects.
Navind
This guy hails all the way from Mauritius and speaks 7 languages in total! He’s got a fun-loving, positive attitude, which we think contribute to his youthful looks – his well-kept secret. Navind does account management for small and medium size partners worldwide, particularly German-speaking countries. Which means he helps make businesses grow, takes care of partner accounts, and just supports partners in what they may need. Whether it’s marketing advice, upgrades, migrations and more.
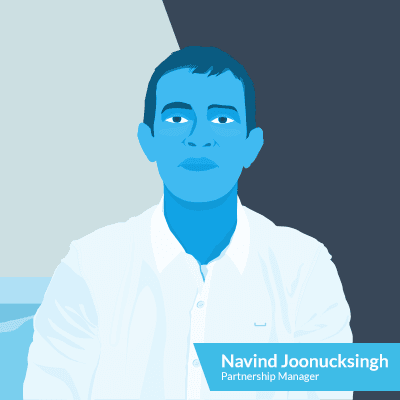
Partner Languages: German, French, Italian, Hindi, Spanish, and English.
Fun fact about Navind: Takes his siesta every day, no matter what or where.
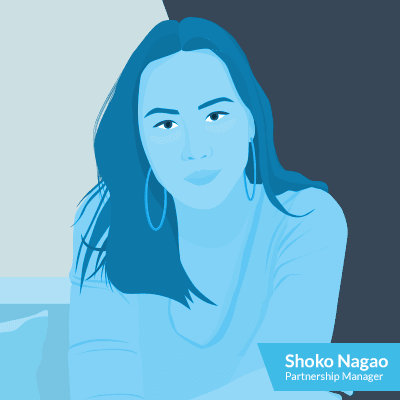
Partner Languages: English and Japanese.
Fun fact about Shoko: There are only fun facts about Shoko.
Shoko
Shoko lives in Europe now but comes all the way from Japan. So she mainly focuses on our APAC, Japan and UK-based partners. Shoko says that she is one of the escalation points or main contacts for partners. She’ll propose new business opportunities, discuss price and agreement queries, and arrange demos of new versions and extensions. Plus, she handles event invites and so on so our partners will never have to miss a beat.
“If you have issues or concerns about your business, please come to us and we’ll do our best to provide a solution for you. Your business growth is our business growth!”
Marin
Half Croatian and half Italian – it’s no surprise that Marin focuses on Partners in the Mediterranean region, as well as in the Americas. Like the rest of the team he manages partner relations and provides strategic consulting and go-to-market guidance to major hosting and cloud firms worldwide. He’s happy that he’s helped established industry leaders in order to develop their services and make their businesses ready for the commercial and technological challenges of the future.
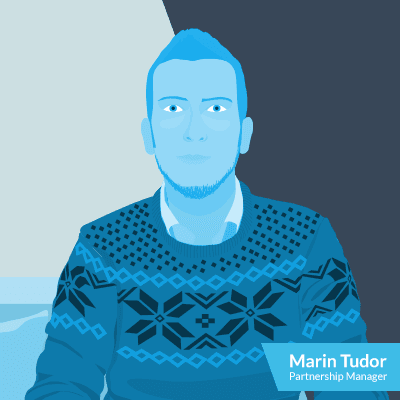
Partner Languages: English, Italian, French, Spanish, Portuguese, Russian, Serbo-Croatian, German.
Fun fact about Marin: He’s working on adding langugae 9 to his portfolio – Turkish!
Partner Languages: English and Russian.
Fun fact about Rubina: Loves fish and Thai food.
Rubina
Another contact point for partners in team is Rubina. She’s from Armenia and supports English and Russian speaking partners, with special focus on a Benelux. She’ll give counseling for any of the benefits mentioned in our Partner Program. Generally, the Partner Success Team act as Sales Consultants/Experts. Meaning they’ll inform you of market trends and what’s happening in the industry. And they’ll help you stay competitive.
The Plesk Partner Program: Do you want in?
“We help Plesk Partners with any commercial stuff, like contracts, prices and new business opportunities. Even setting up specific promotions and campaigns. We inform them about the latest Plesk news, products and extensions. And help them stay on the latest versions available with upgrades and migrations.
We can arrange demos with our Sales Engineer and help them implement Plesk into their offerings. And also suggest how to bundle and position Plesk on websites.”
– Tess.
Truthfully, these guys make the whole Partner Program possible. And we’re happy to have given you a peek behind the curtain. In order to have you see who’s making the magic happen for you and your prospective business.
So what now?
A couple of options for you. If you’re not a partner yet, there are some benefits you’re definitely missing out on. So start with the downloadable partner brochure. Or if you’re ready to learn more about becoming a partner and get in touch, click below.
Already a partner? Then enjoy our Partner video library that we’re frequently uploading for you to get the best out of your Plesk.
The post Meet the Plesk Partner Success Team – Behind the Scenes [Video] appeared first on Plesk.
(May 30) Update to 1.91 – fixes double-free in read_gif