Ubuntu: 1860-1: libxinerama vulnerability
(Jun 5) Several security issues were fixed in libxinerama.
(Jun 5) Several security issues were fixed in libxinerama.
Netcraft blocked a Twitter phishing site being served from multiple Facebook Applications on 6th June. Visitors to the Facebook applications were requested to enter their Twitter credentials in order to view a “Twitter Video” application. On submission of the fake twitter login form, the user is redirected to YouTube.
Links to the phishing attack were spread via both public tweets and direct messages.
A Twitter direct message can only be sent to and from users who are following each other which lends credence to the message and the link it contains. The message entices the recipient to visit the fraudulent Facebook application: “I’m turning off my page if no one comes farward [sic] regarding this. https://apps.facebook.com/165922313586222“.
Facebook — a trusted website which is served over HTTPS — is a useful medium for a fraudster; a Facebook user may be accustomed to seeing legitimate third-party authorisation forms on the social network making a fake login form all the more convincing. Netcraft has also observed similar attacks targeting Facebook itself which are being spread via Facebook statuses.
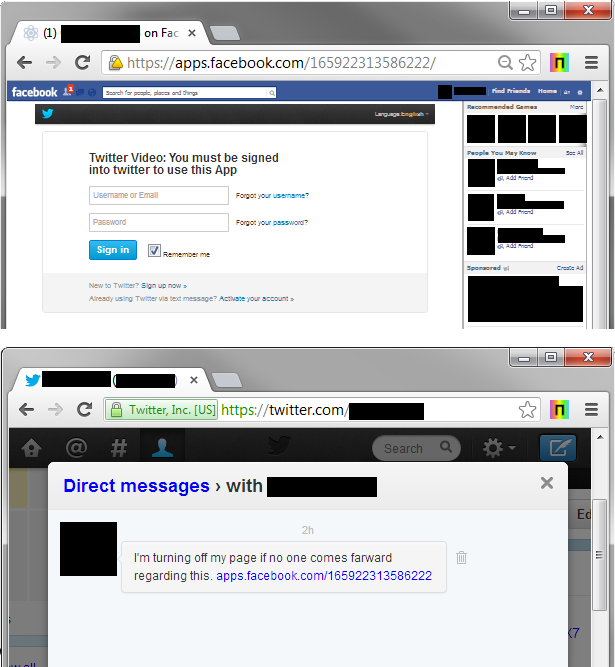
Twitter phishing via Facebook Apps and Twitter direct messages
Facebook Apps are not hosted on Facebook servers, instead they are hosted by a third party provider.
The Facebook Apps involved in this phishing attack were hosted on Heroku and included on facebook.com via an iframe.
In September 2011 Facebook partnered with Heroku, simplifying the process of setting up a new Heroku hosting account and Facebook App down to a few clicks. Heroku provides free accounts which are attractive for fraudsters wishing to host phishing attacks on Facebook.
The Facebook App at Heroku has a further iframe showing the actual fake login form, which is hosted at another hosting provider Joe’s Datacenter. Both Facebook and the Facebook App hosted at Heroku are served using HTTPS but the final iframe is not, causing some browsers to display an insecure content warning.
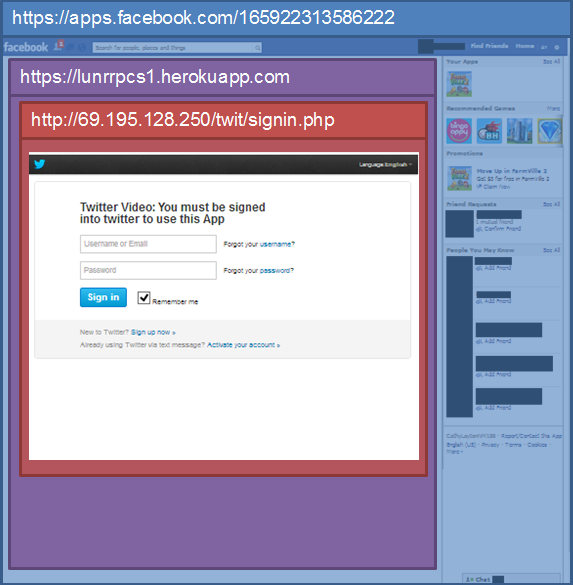
Structure of the phishing attack: the fake twitter login form is included in an iframe within the Heroku-hosted Facebook App. The Facebook App is then including on facebook.com within another iframe.
Internet Explorer 9+ blocks HTTP iframes on HTTPS pages by default as it considers them as Mixed Active Content.
Firefox currently hides the padlock when viewing mixed content, but does not block it. Firefox 23, due for release later this month, will automatically block iframes when it introduces Mixed Active Content blocking.
In Google Chrome, iframes are currently considered passive rather than active, so the padlock icon displays a warning but the content is not blocked. Chrome 29 will switch to treating iframes as Mixed Active Content and block them by default.

Mixed Active Content Blocking in IE10, Pre-release Firefox Nightly, Pre-release Chromium
On 6th June, Netcraft observed the following events (times are GMT). Netcraft had access to both a compromised Twitter account and a second Twitter account which was targeted by the first.
Social network credentials are particularly appealing to fraudsters as they have a built-in method to spread the attack without further involvement from the fraudster. Some features, such as attached third-party applications, can make a compromised account even more valuable to a fraudster. Authentication forms of the type imitated in this attack are common and train users to expect to see social media login forms triggered from websites other than that of the social network itself. Despite this attack asking for Twitter credentials within a Facebook App, the fraudster was still able to gather twitter account credentials and use them to further spread the attack using twitter direct messages and tweets.
You can protect yourself against phishing attacks by installing Netcraft’s Anti-Phishing Extension. You can help protect the internet community by reporting potential phishing sites to Netcraft by email to [email protected] or at http://toolbar.netcraft.com/report_url. Netcraft can also help protect both brand owners and hosting companies.
(Jun 5) Several security issues were fixed in libxfixes.
(Jun 5) Several security issues were fixed in libxext.
(Jun 5) Several security issues were fixed in libxt.
59 queries. 8.25 mb Memory usage. 0.482 seconds.