(Jun 5) Several security issues were fixed in libxres.
(Jun 5) Several security issues were fixed in libxvmc.
(Jun 5) Several security issues were fixed in libxi.
Phishing attack hosted on police site with an SSL certificate
The Malaysian government’s Police Portal (Johor Contingent) is currently hosting a phishing attack against PayPal on its secure website https://www.polisjohor.gov.my (Site Report). Phishing sites using SSL certificates can piggyback on the trust instilled by browser indicators, such as the padlock icon, to trick potential victims into revealing sensitive information such as their username and password. The SSL certificate used for this phishing attack is irrevocable in some major browsers including Firefox (due to the lack of an OCSP URL in the certificate) and Safari (which doesn’t check revocation by default).
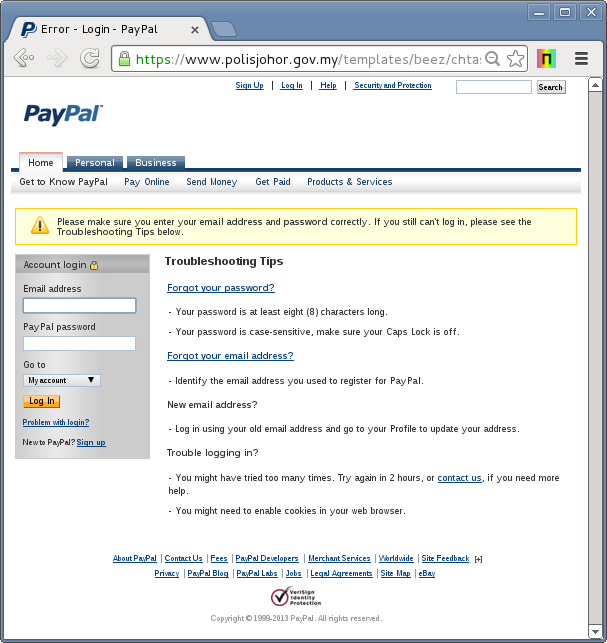
A phishing site targeting PayPal hosted on the Malaysian Police’s web site which is available over HTTPS.
Fraudsters often use a compromised third party website to host their phishing attack rather than obtaining web hosting directly. By compromising an existing trusted website the fraudster can avoid paying for a potentially suspicious domain name or SSL certificate himself. For example, registering or obtaining an SSL certificate for paypaal.com could draw unwanted attention if the registrar or SSL certificate authority is already conscious of the risk posed by this type of domain name.
The presence of an SSL certificate on a website hosting a phishing site is far from unusual. In May 2013, Netcraft identified 234 trusted SSL certificates on websites with at least one known phishing site. Of these, 67 were issued by Symantec (including the polisjohor.gov.my certificate) which may not be surprising given its leading position in the SSL certificate market. Comodo and Go Daddy had a similar number of such certificates discovered by Netcraft, 42 and 46 respectively. Extended Validation (EV) certificates could be especially valuable to a fraudster as they are designed explicitly to increase the perceived trustworthiness of websites which have passed the validation process by displaying additional indicators such as green bar. During May 2013, Netcraft identified five EV certificates being used on potentially compromised websites: two signed by Symantec and one each signed by Comodo, DigiCert, and Go Daddy.
The SSL certificate for polisjohor.gov.my was issued by GeoTrust (a Symantec brand) back in 2011 and is valid for several more months. If Symantec wished to revoke the certificate to make the site inaccessible over HTTPS it could do so by updating its Certificate Revocation List or by providing on-demand OCSP responses noting its revocation. As examined by Netcraft recently, the current treatment of revocation in many major browsers leaves some room for improvement: this certificate does not contain an OCSP URL so is irrevocable in Firefox. Even if the CA wanted to, it could not directly prevent further use of the certificate in Firefox. Safari users are left unprotected by default as the revocation checking has to be explicitly enabled.
Netcraft offers Phishing alerts to CAs to provide timely alerts to the CA about potential misuse of a certificate. Having access to timely, professionally validated alerts when phishing attacks occur can allow the CA to provide the first alert of a compromise to the webmaster. Both the CA and the webmaster are then able to respond appropriately to the potential compromise, safeguarding the reputation of both parties.
(Jun 5) Several security issues were fixed in libxxf86vm.