Following check item has been added:
WordPress 3.6 Beta 1
WordPress 3.6 Beta 1 is now available!
This is software still in development and we really don’t recommend that you run it on a production site — set up a test site just to play with the new version. To test WordPress 3.6, try the WordPress Beta Tester plugin (you’ll want “bleeding edge nightlies”). Or you can download the beta here (zip).
We’ve been working for nearly three months and have completed all the features that are slated for this release. This is a bit of a change from the betas of previous release cycles. I felt very strongly that we shouldn’t release a beta if we were still working on completing the main features. This beta is actually a beta, not an alpha that we’re calling a beta. If you are a WordPress plugin or theme developer, or a WordPress hosting provider, you should absolutely start testing your code against this new version now. More bugs will be fixed, and some of the features will get polished, but we’re not going to shove in some big new feature. We’re ready for you to test it, so jump in there! The more you test the beta, the more stable our release candidates and our final release will be.
As always, if you think you’ve found a bug, you can post to the Alpha/Beta area in the support forums. Or, if you’re comfortable writing a reproducible bug report, file one on the WordPress Trac. There, you can also find a list of known bugs and everything we’ve fixed so far.
Here’s what’s new in 3.6:
- Post Formats: Post Formats now have their own UI, and theme authors have access to templating functions to access the structured data.
- Twenty Thirteen: We’re shipping this year’s default theme in our first release of the year. Twenty Thirteen is an opinionated, color-rich, blog-centric theme that makes full use of the new Post Formats support.
- Audio/Video: You can embed audio and video files into your posts without relying on a plugin or a third party media hosting service.
- Autosave: Posts are now autosaved locally. If your browser crashes, your computer dies, or the server goes offline as you’re saving, you won’t lose the your post.
- Post Locking: See when someone is currently editing a post, and kick them out of it if they fall asleep at the keyboard.
- Nav Menus: Nav menus have been simplified with an accordion-based UI, and a separate tab for bulk-assigning menus to locations.
- Revisions: The all-new revisions UI features avatars, a slider that “scrubs” through history, and two-slider range comparisons.
Developers: You make WordPress awesome(er). One of the things we strive to do with every release is be compatible with existing plugins and themes. But we need your help. Please test your plugins and themes against 3.6. If something isn’t quite right, please let us know. (Chances are, it wasn’t intentional.) If you’re a forward-thinking theme developer, you should be looking at implementing the new Post Format support in some of your themes (look to Twenty Thirteen for inspiration).
We’re looking forward to your feedback. If you break it (i.e. find a bug), please report it, and if you’re a developer, try to help us fix it. We’ve already had more than 150 contributors to version 3.6 — it’s not too late to join the party!
Mulberry — well known for its luxury fashion accessories — is currently being impersonated by fake online stores which have successfully promoted themselves to the first page of search engine results by planting malign JavaScript on hacked websites.
The hacked sites display various descriptions of Mulberry products, and also include hyperlinks to the fake Mulberry sites. Both help to make the fake sites seem more relevant to search engines; indeed, the fake stores can even be reached from the first page of organic Google search results for the search term "Mulberry".

The injected scripts are sourced from an external site hosted in China, but which uses the .la country code top-level domain. This ccTLD belongs to the Lao People’s Democratic Republic, but is actively marketed as a top-level domain for the US city of Los Angeles. Although the fake store associated with the above screenshot uses a UK ccTLD, it is actually hosted by
root S.A. in
Luxembourg, and shares
the same netblock as kim.com and several bittorrent sites, including a mirror of
The Pirate Bay, allowing the site to be accessed from countries where ISPs were ordered to implement blocks against the original Pirate Bay site.
Such underhanded methods of search engine optimisation (SEO) are not unusual, and can potentially outperform traditional spam-based marketing. For instance, there is likely to be a much larger conversion rate among customers who are actively searching for a specific product than there would be among recipients of spam, many of whom would have no intention of buying anything, and – thanks to spam filters – may not even receive the spam in the first place. With such low returns on spam-based marketing, a huge number of emails would need to be sent in order to achieve a worthwhile return, which would only serve to draw more – possibly unwanted – attention to a fake site.
Some of the hacked sites which appear on the first page of a Google search for “Mulberry” lend further credibility to the scam, making it appear as though the products for sale have received thousands of reviews and near-perfect ratings. However, clicking on these links causes the user to be redirected to one of the fake stores, such as http://www.mulberryeshop.co.uk.

Even if you arrive at a website via a trusted search engine, Netcraft’s site reports can help you make informed decisions about whether that site itself should be trusted. For example, Netcraft’s site report awards a Risk Rating of 9/10 to www.mulberryeshop.co.uk, whereas the legitimate site, www.mulberry.com, has a rating of 0/10. Such ratings are conveniently accessible to users of the
Netcraft browser extension, which is available for Firefox and Chrome.
Other obvious clues to look out for are the lack of an encrypted HTTPS connection when logging in to the site, and the WHOIS record for the domain reveals that “the registrant is a non-trading individual who has opted to have their address omitted from the WHOIS service.”
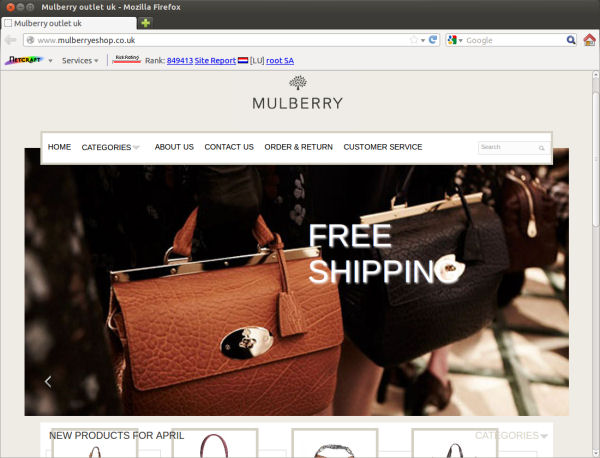
Brand owners can also take the initiative to protect both themselves and their customers. The fake store shown above was detected last month by Netcraft’s
phishing, identity theft and fraud detection service, demonstrating how brand owners can receive early warnings of such attacks.
Mulberry’s extraordinary success over the past five years (LON:MUL) has made it an attractive brand to target, even though its shares dropped by 16% last month. This drop followed a profit warning, which revealed weaker than anticipated trading post-Christmas. It is plausible that a multitude of fake stores, with good search engine rankings, could have contributed towards this reduction in revenue.
(Apr 2) Applications using poppler could be made to crash or possibly run programsas your login if they opened a specially crafted file.
(Apr 2) Several security issues were fixed in the kernel.