(Aug 21) Updated kernel packages that fix one security issue and several bugs are now available for Red Hat Enterprise Linux 5. The Red Hat Security Response Team has rated this update as having low [More…]
Over the years the Internet community has been taught that one of the key steps in protecting their personal information on the Internet is to ensure that it is entered only over an encrypted connection, perhaps by looking for the lock symbol in the browser address bar or web addresses beginning with https://. As a result, phishing attacks which make use of SSL certificates are especially dangerous as most users associate the presence of a valid SSL certificate with an increased level of assurance. Such attacks erode the reputation of Certificate Authorities and SSL certificates, which makes identifying and revoking maliciously used certificates a material issue.
Netcraft’s anti-phishing feed has blocked over 5 million unique phishing sites to date, receiving over 4 reports a minute from our reporter community, and while the majority of phishing attacks run over HTTP, a significant number run on sites for which SSL certificates have been issued. In July 2012 alone, Netcraft found 505 unique valid certificates on blocked sites.
The following table, produced for the Netcraft SSL Survey, shows the number of unique valid certificates returned by phishing sites that were blocked by Netcraft in July 2012:
| Certificate Authority (CA) | Unique certificates | …with matching Common Names | …and accessed by https:// |
|---|---|---|---|
| Symantec | 216 | 41 | 21 |
| Comodo | 130 | 16 | 7 |
| Go Daddy | 67 | 19 | 8 |
| Other | 41 | 11 | 6 |
| GlobalSign | 39 | 2 | 1 |
| DigiCert | 12 | 2 | 2 |
The columns of the table are ordered left to right by trustworthiness, as using a valid SSL certificate is not always enough to trick a user into trusting a phishing website and two further conditions have to be met:
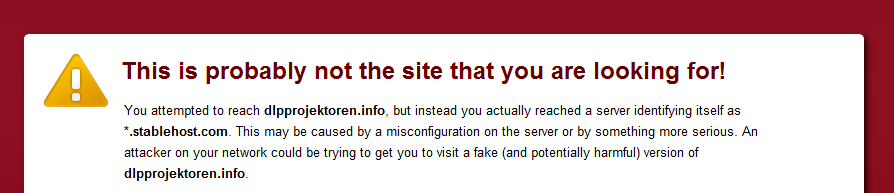
- The Subject Common Name of the certificate has to match the hostname of the phishing site that returned it. Some sites will return the hosting company’s certificate when requested over HTTPS. As most modern browsers display warnings when a non-matching certificate is encountered (pictured below), such certificates only serve to make the user more suspicious instead of increasing the perceived security of the site.
- The phishing attack has to actively use the SSL certificate by including https:// in the phishing URL. Having a valid SSL certificate does not make a phishing site appear more trustworthy if victims only access it over HTTP.
Fraudsters will often host their phishing content on a compromised website and so can make use of the website’s legitimate certificate, however they may not have realized that SSL services are available and so serve the content over HTTP. None of the certificates found on phishing sites in this period appeared to have been issued specifically for the purpose of phishing.
Taking Certificate Authority market shares into consideration, Go Daddy has a lower proportion of its SSL certificates used in phishing attacks than the other large CAs, in part because it provides the hosting for a large proportion of the certificates which they issue and is a long term user of Netcraft’s feed to remove phishing attacks.
(Aug 18) Several denial-of-service vulnerabilities have been discovered in Xen, the popular virtualization software. The Common Vulnerabilities and Exposures project identifies the following issues: [More…]
Plesk Automation team is pleased to introduce an improved Installation Script of the PPA. Thanks to all for feedback!
Plesk Automation team is pleased to introduce an improved Installation Script of the PPA. Thanks to all for feedback!