The following bugs have been fixed:
[-] Blank pages appear randomly in plesk GUI, because of short field “data” in “session” table. Data type of field “data” in “sessions” table in “psa” database was changed from “TEXT” to “MEDIUMTEXT”. (92138)
[-] Domains are not visible in admin panel if at least on domain with forwarding hosting does not have ‘http://’ in URL. (91218)
[-] Customizing of domain’s PHP Settings in panel.ini has no effect in GUI if parameter name contains a dot. (100155)
The second release candidate for WordPress 3.4 is now available. Since RC1, we’ve made a few dozen final changes.
Our goal is to release WordPress 3.4 early next week, so plugin and theme authors, this is likely your last chance to test your plugins and themes to find any compatibility issues before the final release. We’ve published some resources on the development blog to help you prepare.
If you think you’ve found a bug, you can post to the Alpha/Beta area in the support forums. Or, if you’re comfortable writing a reproducible bug report, file one on WordPress Trac. Known issues that crop up will be listed here, but we’re hoping for a quiet few days so we can get some great features into your hands next week!
To test WordPress 3.4, try the WordPress Beta Tester plugin (you’ll want “bleeding edge nightlies”). Or you can download the release candidate here (zip). Be sure to visit  → About for an updated list of features and under-the-hood changes.
→ About for an updated list of features and under-the-hood changes.
For many years installing and using cPanel & WHM has involved compiling software on-demand. Want Apache and PHP? Run /scripts/easyapache, which builds those and all dependencies from source. Want perl installed? Download and run the perl installer from httpupdate.cpanel.net, which installs perl from source. While compiling from source has its benefits, it also has its drawbacks.
The drawbacks are more obvious when you consider what cPanel & WHM attempts to do with compile-on-demand. We are automating this on thousands of servers, each with their own subtle differences (and some no-so-subtle). A non-trivial portion of our development effort, bug fixing and support requests are consumed by getting source compilation working in environments under other peoples (yours) control. We decided this needed to change. Hence in 11.34 we are switching our model from compile-on-demand to delivery of pre-compiled RPM packages.
What is involved in this change
For many years we’ve provided applications via RPM. For example MySQL, Dovecot, and Exim. In 11.34 we are adding over 800 additional RPMs. These RPMs provide:
- perl 5.14
- all the perl modules that scripts/checkperlmodules formerly installed
- PHP 5.3 for cPanel & WHM
- rrdtool
- all the pear packages needed for Horde, Roundcube, phpMyAdmin, Logaholic and Squirrelmail
- the encoders used by internal PHP
- nearly everything in /usr/local/cpanel/src
The vast majority of the RPMs are for perl and CPAN modules (801 at last count).
New RPMs will have the naming convention of cpanel-APPLICATION-APPMAJORVERSION-APPVERSION-CPANELPATCH-CPANELVERSION. For example:
cpanel-perl-514-5.14.2-0.cp1134
Broken into its parts we have:
- cpanel-perl: The application is perl
- 514: perl major version of 5.14
- 5.14.2: The specific version of perl in the RPM
- -0: We have not applied any patches, therefore we use 0
- cp1134: Built for cPanel & WHM 11.34
All the new RPMs will be installed to /usr/local/cpanel, rather than to the operating system locations (e.g. /usr ). Whenever possible we fulfill dependencies (e.g. libraries) using what the operating system provides. If that is not possible, we provide the dependency ourselves with an RPM.
Along with an expanded set of RPMs we are also providing a tool you can use to reinstall RPMs. This is useful if something is modifying files managed by a package. The tool will tell you the packages that need reinstalled and allows you to perform the reinstall at your convenience.
How Something is installed
Does this mean you will find scripts like perlup, internalphpup and so forth in 11.34? No. In fact all the scripts that install the current RPMs (e.g mysqlup, eximup) are gone in 11.34. Instead RPMs are tied to the product version and are installed by our “rpm.versions” system. This system behaves somewhat like yum, or apt-get, in that you are able to configure repositories and install software from them. The rpm.versions system was introduced in 11.30, but for 11.34 is completely overhauled. More information on that later.
By and large RPM installation is handled by upcp. For now this is acceptable as the only RPMs we are delivering are required by the product. Eventually we want to provide optional RPMs (e.g. git, subversion, etc) that you can elect to install. When we reach that stage tools, both command line and graphical, will be developed to facilitate package installation outside of upcp.
Source Compiles
All the source RPMs will be provided on our mirrors. Customers that want to apply patches to the software we provide, or just like compiling software they use, will need to obtain the source RPM and rebuild it. If you want to do this for more than one server, then you will be able to use our rpm.version system so your cPanel & WHM servers install your custom package from a central location.
What is not Involved in this Change
Not everything will switch to delivery via RPM packages. EasyApache will still build Apache et al. from source. cPanel & WHM itself will not be delivered via RPM in this release.
The Benefits
Fresh installs will see a 30% reduction (or better) in installation time. This is due to installing perl, and necessary CPAN modules, from RPM rather than building them from source.
Upgrades should also see a reduction in time, in the long term, as new applications and dependency updates will be fulfilled via RPM packages, rather than building from source during the upgrade.
The rpm.version system gives you a simple way of deploying custom software directly as part of the cPanel & WHM installation and upgrade.
Removal of problems stemming from automated source builds in wildly diverse environments.
Re-installing perl is a matter of re-installing a package, rather than building from source and forcing the reinstallation of a bunch of CPAN module.
Applications and dependencies delivered with cPanel & WHM will be in one location, /usr/local/cpanel, rather than strewn all over the file system(s). The long term goal is to have everything installed to /usr/local/cpanel. For 11.34 only the new RPMs adhere to this.
More
There is far more to these changes than what is detailed here. In the coming weeks we’ll share more information on:
- perl 5.14 in cPanel & WHM
- Changes to the internal PHP
- rpm.versions system
- Changes to how cPanel & WHM are updated to make it more robust
Please discuss this article on our forum.
| Rank | Company site | OS | Outage hh:mm:ss |
Failed Req% |
DNS | Connect | First byte |
Total |
| 1 | www.cwcs.co.uk | Linux | 0:00:00 | 0.003 | 0.327 | 0.214 | 0.337 | 1.018 |
| 2 | ReliableServers.com | Linux | 0:00:00 | 0.007 | 0.250 | 0.081 | 0.167 | 0.244 |
| 3 | iWeb Technologies | Linux | 0:00:00 | 0.017 | 0.116 | 0.084 | 0.167 | 0.167 |
| 4 | Hosting 4 Less | Linux | 0:00:00 | 0.017 | 0.152 | 0.094 | 0.187 | 0.386 |
| 5 | Datapipe | FreeBSD | 0:00:00 | 0.024 | 0.174 | 0.025 | 0.050 | 0.076 |
| 6 | www.choopa.com | Linux | 0:00:00 | 0.024 | 0.203 | 0.084 | 0.172 | 0.246 |
| 7 | www.catalyst2.com | Linux | 0:00:00 | 0.024 | 0.372 | 0.097 | 0.201 | 0.300 |
| 8 | www.dinahosting.com | Linux | 0:00:00 | 0.024 | 0.162 | 0.117 | 0.234 | 0.234 |
| 9 | Qube Managed Services | Linux | 0:00:00 | 0.030 | 0.143 | 0.100 | 0.201 | 0.201 |
| 10 | www.memset.com | Linux | 0:00:00 | 0.037 | 0.101 | 0.096 | 0.192 | 0.382 |
The most reliable hosting company during May was CWCS — a UK-based company offering a variety of web and managed hosting services from their own data centres in Nottingham. Advertising a “100% uptime guarantee” CWCS top the chart for May after responding to all but one request.
ReliableServers.com remains in the top ten for the third month in a row, placing second — 6 places higher than last month. Offering dedicated hosting and colocation from their two New Jersey data centres — located in Newark and North Bergen — ReliableServers.com also guarantees 100% uptime.
Seeing their highest placing this year, iWeb Technologies are May’s third most reliable hosting company. Their four data centres in the Montréal area are supplied by 7 different network providers to ensure high reliability.
During May nine out of the ten most reliable companies were using Linux servers with the remaining company, Datapipe, last month’s most reliable company, running FreeBSD.
Netcraft measures and makes available the response times of around forty leading hosting providers’ sites. The performance measurements are made at fifteen minute intervals from separate points around the internet, and averages are calculated over the immediately preceding 24 hour period.
From a customer’s point of view, the percentage of failed requests is more pertinent than outages on hosting companies’ own sites, as this gives a pointer to reliability of routing, and this is why we choose to rank our table by fewest failed requests, rather than shortest periods of outage. In the event the number of failed requests are equal then sites are ranked by average connection times.
Information on the measurement process and current measurements is available.
In the June 2012 survey we received responses from 697,089,482 sites, a growth of 5.1% or 34M sites since last month.
All major web server vendors experienced an increase in hostnames this month. After a loss of 17.5M hostnames last month Apache saw the largest growth this month with an increase of 22.8M hostnames. The second largest growth was seen by Microsoft with an increase of 3.5M hostnames. This, however, still resulted in a loss in the market share for Microsoft. nginx, after nine consecutive months of market share growth, also experienced a loss in market share albeit gaining 2.1M hostnames.
The 6th of June 2012 is the World IPv6 launch day. The event is organized by the Internet Society and it is aiming to promote the widespread usage of the protocol. This month’s survey received IPv6 AAAA results for over 7M hostnames, mapping to 105k distinct IPv6 addresses. Apache was found running on the majority of these hostnames (6.2M), followed by nginx with 398k hostnames.
August 1995 – June 2012

August 1995 – June 2012

| Developer | May 2012 | Percent | June 2012 | Percent | Change |
|---|---|---|---|---|---|
| Apache | 425,631,721 | 64.20% | 448,452,703 | 64.33% | 0.13 |
| Microsoft | 92,406,480 | 13.94% | 95,891,537 | 13.76% | -0.18 |
| nginx | 70,764,248 | 10.67% | 72,881,755 | 10.46% | -0.22 |
| 21,264,616 | 3.21% | 22,464,345 | 3.22% | 0.02 |
June 2000 – June 2012
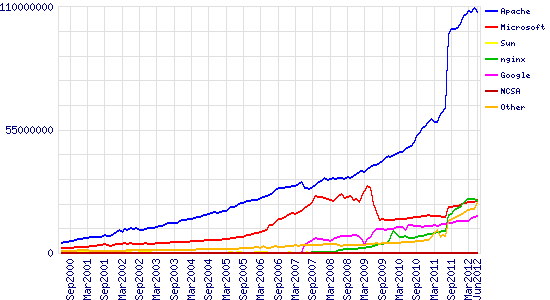
| Developer | May 2012 | Percent | June 2012 | Percent | Change |
|---|---|---|---|---|---|
| Apache | 109,278,620 | 57.02% | 107,485,139 | 55.73% | -1.29 |
| Microsoft | 22,803,442 | 11.90% | 23,464,661 | 12.17% | 0.27 |
| nginx | 23,938,754 | 12.49% | 23,114,450 | 11.98% | -0.51 |
| 15,855,806 | 8.27% | 16,473,290 | 8.54% | 0.27 |
For more information see Active Sites
September 2008 – June 2012
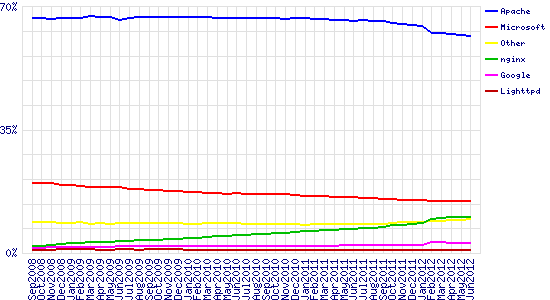
| Developer | May 2012 | Percent | June 2012 | Percent | Change |
|---|---|---|---|---|---|
| Apache | 617,430 | 62.02% | 614,721 | 61.75% | -0.27 |
| Microsoft | 146,974 | 14.76% | 147,054 | 14.77% | 0.01 |
| nginx | 100,417 | 10.09% | 102,449 | 10.29% | 0.20 |
| 29,071 | 2.92% | 28,498 | 2.86% | -0.06 |