In the June 2012 survey we received responses from 697,089,482 sites, a growth of 5.1% or 34M sites since last month.
All major web server vendors experienced an increase in hostnames this month. After a loss of 17.5M hostnames last month Apache saw the largest growth this month with an increase of 22.8M hostnames. The second largest growth was seen by Microsoft with an increase of 3.5M hostnames. This, however, still resulted in a loss in the market share for Microsoft. nginx, after nine consecutive months of market share growth, also experienced a loss in market share albeit gaining 2.1M hostnames.
The 6th of June 2012 is the World IPv6 launch day. The event is organized by the Internet Society and it is aiming to promote the widespread usage of the protocol. This month’s survey received IPv6 AAAA results for over 7M hostnames, mapping to 105k distinct IPv6 addresses. Apache was found running on the majority of these hostnames (6.2M), followed by nginx with 398k hostnames.
August 1995 – June 2012

August 1995 – June 2012

| Developer | May 2012 | Percent | June 2012 | Percent | Change |
|---|---|---|---|---|---|
| Apache | 425,631,721 | 64.20% | 448,452,703 | 64.33% | 0.13 |
| Microsoft | 92,406,480 | 13.94% | 95,891,537 | 13.76% | -0.18 |
| nginx | 70,764,248 | 10.67% | 72,881,755 | 10.46% | -0.22 |
| 21,264,616 | 3.21% | 22,464,345 | 3.22% | 0.02 |
June 2000 – June 2012
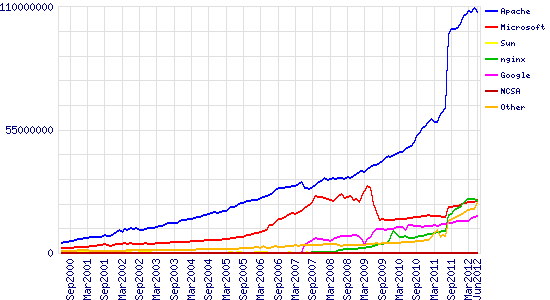
| Developer | May 2012 | Percent | June 2012 | Percent | Change |
|---|---|---|---|---|---|
| Apache | 109,278,620 | 57.02% | 107,485,139 | 55.73% | -1.29 |
| Microsoft | 22,803,442 | 11.90% | 23,464,661 | 12.17% | 0.27 |
| nginx | 23,938,754 | 12.49% | 23,114,450 | 11.98% | -0.51 |
| 15,855,806 | 8.27% | 16,473,290 | 8.54% | 0.27 |
For more information see Active Sites
September 2008 – June 2012
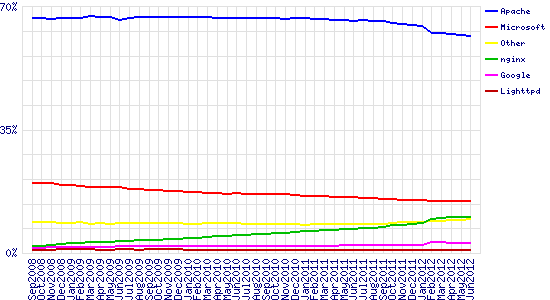
| Developer | May 2012 | Percent | June 2012 | Percent | Change |
|---|---|---|---|---|---|
| Apache | 617,430 | 62.02% | 614,721 | 61.75% | -0.27 |
| Microsoft | 146,974 | 14.76% | 147,054 | 14.77% | 0.01 |
| nginx | 100,417 | 10.09% | 102,449 | 10.29% | 0.20 |
| 29,071 | 2.92% | 28,498 | 2.86% | -0.06 |