The following bugs have been fixed:
[-] Atmail upgrade failed on action ‘Inserting old Atmail database data…’
[-] Automatic key update fails if KAV additional key is installed, but KAV itself is not.
[-] Can not connect service nodes using CLI gate
[-] Cannot change FTP user’s password if “Setup of potentially insecure web scripting options” disabled on subscription
We would like to introduce you Plesk Troubleshooter Posters.
In knowledge base article you can find them for Linux and Windows versions of Plesk.
Please feel free to discuss these posters in special thread on Parallels Forum http://forum.parallels.com/showthread.php?t=246206
The following bugs have been fixed:
[-] Atmail upgrade failed on action ‘Inserting old Atmail database data…’
[-] Automatic key update fails if KAV additional key is installed, but KAV itself is not.
[-] Can not connect service nodes using CLI gate
[-] Cannot change FTP user’s password if “Setup of potentially insecure web scripting options” disabled on subscription
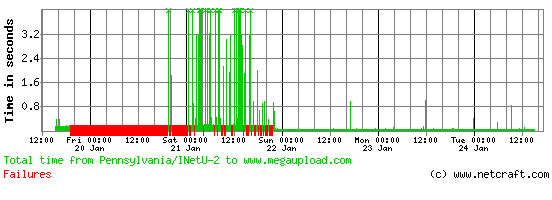
The United States Department of Justice appears to be under attack for the second time since the popular Megaupload file sharing site was taken down. The group Anonymous appears to be carrying out this latest attack in protest against the Anti-Counterfeiting Trade Agreement (ACTA)
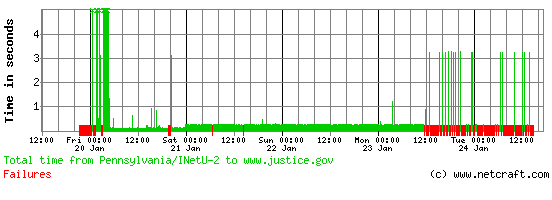
In its Mega Song music video, which was released last month, Megaupload claimed the site had 1 billion users and accounted for 4% of all traffic on the internet. www.megaupload.com was the 77th busiest site according to the Netcraft Toolbar. The company’s main website was hosted by Carpathia Hosting, but now displays an FBI anti-piracy warning hosted by Amazon. The warning explains, “This domain name associated with the website Megaupload.com has been seized pursuant to an order issued by a U.S. District Court.” Despite the static nature of the warning page, it appears to have struggled with the amount of traffic it was receiving over the weekend:
In order to know that you need to add an ID to a rule you will have already found the error in the logs. To white list the rule this requires the rule to have an ID. All of the rules are stored in /usr/local/apache/conf/modsec2.user.conf. I usually vim the conf file and / to search for the pattern match that the error lists. You can also go to the line number listed in the error.
vim /usr/local/apache/conf/modsec2.user.conf
When you find the correct rule and line you will need to add an ID. It doesn’t really matter what number you assign to it as long as it already is not in the file. the syntax to add the ID would be as follows:
….rule” “ID:300018”
Save the file and now you can white list the ID number.